Lab 4: Introduction to Buffer Overflows
In this lab, you will be introduced to Buffer Overflows.
Please follow the instructions given below, or print
out this PDF file :
Setup
1. wget http://www.netlab.uky.edu/~griff/classes/cs485/handouts/labs/l4/bufdemo.tar
2. tar -vxf bufdemo.tar
3. cd bufdemo; cat bufdemo.c; /* Now read the program */
4. make
5. ./bufdemo
6. Type '123' when prompted. You should see the expected output of:
Abuf = ''
Bbuf = '123'
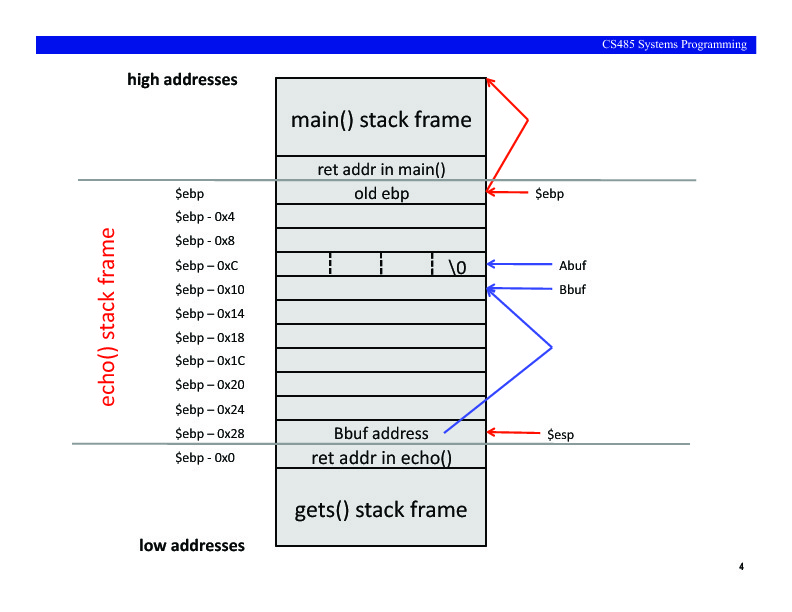
Basic Buffer Overflow Exercises
Use the stack layout shown below to do the following exercises. As you do
each of the exercises, use the script command to create a text file with the
output from running the program. To type in answers to the "why"
questions, run 'cat > /dev/null' and then type in your answer. After you
have typed in your answer, type Control-D (end of file).
1. Find an input string that will result in the program printing:
Abuf = ''
Bbuf = '1234'
2. Find an input string that will result in the program printing:
Abuf = '56'
Bbuf = '123456'.
3. Give 123456789012345 as input. What is the output? Why?
4. Give 1234567890123456 as input. What is the output? Why?
5. Run the program under gdb (saving the output via script) and
set a breakpoint just before returning from echo(). Run the
program and type 12345678901234567890 as the input. Single step (using the
'mynexti' function below) past the return from echo(). Does the echo()
procedure return to main()? Explain what is happening. Include the output
captured using script along with your answer.
Note: To single step through the instructions
you may find it useful to define the following function
define mynexti
nexti
disassemble $pc,+20
end
Using Buffer Overflows to Gain Control
Setup
Download and install a tarball that contains two programs you will need
for this part of the lab. The two programs are
oflow_echo and
hex2raw .
1. wget http://www.netlab.uky.edu/~griff/classes/cs485/handouts/labs/l4/bufexercise.tar
2. tar -vxf bufexercise.tar
3. cd bufexercise
4. chmod a+x hex2raw
5. make all
Instructions
Read the oflow_echo.c program.
Try to find an input
string that will caused the
oflow_echo.c
program to call the "not_called()" procedure.
Note that the "not_called()" procedure is never called in the
oflow_echo.c code, so you will need to use a buffer overflow
attack to get the code to jump to the not_called() procedure.
You will need to create a binary string (called an exploit string
to send as input to the program.
To create an exploit string you can use the
hex2raw
program.
The hex2raw program
can help you generate binary strings. It takes
as input a hex-formatted string. In this format, each byte
value is represented by two hex digits. For example, the string
"012345" could be entered in hex format as "30 31 32 33
34 35". (Recall that the ASCII code for decimal digit i is 0x3i).
The hex characters you pass to hex2raw should be separated by
whitespace (blanks or newlines). I recommend separating different
parts of your exploit string with newlines while you're working on
it. Hex2raw also supports C-style block comments, so you can
mark off sections of your exploit string. For example:
bf 66 7b 32 78 /* mov $0x78327b66,%edi */
If you generate a hex-formatted exploit string in the file "exploit.txt", you
can apply the binary string to oflow_echo in several
different ways:
When you complete the exercises, submit your file via the cs portal
(https://www.cs.uky.edu/csportal).
